BE Computer (2012 Course)
Semester-2, Elective-4(a) February 2016
Software Design methodologies and Testing
Time: 1 hour Marks: 30
Q1) a) Explain COMET and phases of COMET. (5 marks)
- COMET is a use case and object-oriented software development method which uses UML notations to describe the design. The different characteristics such as inheritance, classes of object-oriented language are also used.
- COMET stands for Collaborative Object Modeling and Design Method.
Phases of COMET:
- Requirement modeling phase: In this, core functional requirements are defined. For this, actors and use cases are used.
- Analysis Modeling Phase: In this phase, the static and dynamic models are developed. Static involves class diagrams and their relationships while dynamic model includes dynamic changes of an object.
- Design Modeling Phase: In this phase, entire software architecture is created which involve coding, architectural design patterns, inheritance etc.
- Incremental software construction: For every increment, a subset is selected and constructed.
- Incremental software integration: In this phase, integration testing is performed.
- System testing: In this last phase, the complete system is tested.
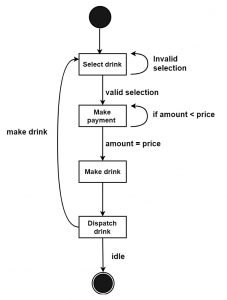
Q1) b) Draw a state machine diagram for the coffee vending machine. (5 marks)
OR
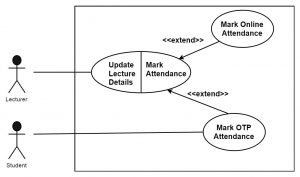
Q2) a) What is extended and include stereotype in use case diagram? Explain with an appropriate example. (5 marks)
Let discuss extend first:
Extend:
- Use case which represents extended functionality is called an extended use case. For representing a precise location in the base use case, an extension point is used.
- Extension occurs when some part of use case is optional and it is required to show the different functionality of the system.
- Also, when the particular condition happens and at that time if you want to display the sub-flow of the system then an extension can occur.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23d0d0d0%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(64.8%2060.2%20172.4)%20scale(31.16138%20102.89189)%22%2F%3E%3Cellipse%20fill%3D%22%23d1d1d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(36.60019%2037.37605%20-18.74612%2018.35699%20207.8%20111.5)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-119.37427%20-199.45987%2044.6639%20-26.7308%2094.7%20161.7)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(53.8376%2011.12432%20-7.01822%2033.96558%20263.2%2079.4)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Fig. Use case for extend relationship
- Through mark attendance, two extensions are created mark online attendance and mark OTA attendance. Here base use case is updated lecture details.
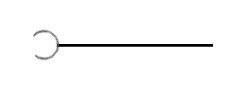
Include:
- Any other use case can use the functionality of include use case. A different use case can include the same functionality by extending it to include use case.
- For an employee, at the time of filling their personal information which will store an employee record, their mobile number is validated with the help of OTP. The id-card use case is also generated for id cards. If employee lost its id- card then he can use its mobile number for making duplicate id card. Here we can include Validate-using-OTP into employee-records and id-generation.
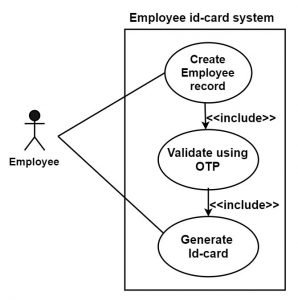
Fig. Inclusion relationship
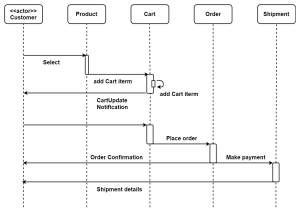
Q2) b) Draw a sequence diagram for online shopping system. (5 marks)
Q3) a) Explain client-server software architecture. Describe multiple client/multiple service architectural patterns with an example. (5 marks)
Client-server architecture:
- In this, client act as requester and server act as a provider for service. The client may require database service or file service etc.
- The server is a combination of software and hardware that host service while service is an application specific functionality.
- Multithreading is used in the server for creating multiple threads for successfully handling of the client request. After serving the request, threads are immediately destroyed. The server can execute one service or multiple services.
- There are three client-server architecture patterns they are:
- Multiple clients and single service.
- Multiple clients and multiple services.
- Multi-tier client service.
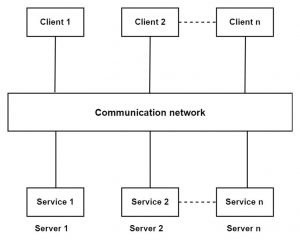
Multiple client/multiple service architectural pattern:
- In this, multiple clients can send a request to multiple servers which host the services and servers can communicate with each other for synchronizing their operation or to take required service from other servers.
- For multiple clients, there are multiple servers/services available therefore it is named as multiple clients multiple service/server.
- A client can communicate with each service concurrently.
%22%20transform%3D%22translate(.6%20.6)%20scale(1.17188)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23c7c7c7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(19.9914%203.48906%20-6.96204%2039.89068%20122.3%20202.2)%22%2F%3E%3Cellipse%20fill%3D%22%23c8c8c8%22%20cx%3D%22124%22%20cy%3D%2288%22%20rx%3D%2231%22%20ry%3D%2214%22%2F%3E%3Cellipse%20fill%3D%22%23cbcbcb%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(16%2057.6%20432.3)%20scale(23.56031%2012.58633)%22%2F%3E%3Cpath%20fill%3D%22%23cecece%22%20d%3D%22M19.8%20216l14.6%203%2016.7-6.6-12.6-44.8z%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Fig. Multiple clients multiple service architecture
- Here, we take the example of banks. Banks have their multiple ATM centers. Suppose, the client has its account in two banks then he can access the service of the first bank from its ATM as well as from the ATM of the second bank and vice versa. Thus, the client can access the multiple services of the same bank as well as from different bank ATM centers.
Q3) b) Describe location transparency and platform transparency with reference to SOA. (5 marks)
The facilities provided by the broker are:
- Location transparency
- Platform transparency
Let discuss them one by one:
Location transparency:
- The client should get the same service irrespective of the change in location of the client.
- If service is moved from one location to another then client should not be aware of this move and client does not have to make configuration changes.
- When such situation happens, the only broker should get the notification and only it has permission to take necessary action.
Platform transparency:
- In this, Client does not need to know the platform details such as software and hardware services.
- There is no need of customization by the client based on the service platform. Also, we can execute services on different software and hardware and the client does not need to maintain the information about each service platform on which service gets executed.
OR
Q4) a) Explain port, provided an interface and required interface with an example. (6 marks)
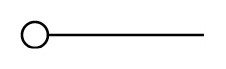
Port:
- It is used for connection of two components through interfaces.
- It is a physical entity.

Fig. Port
Provided Interface:
- It specifies the operation that components must fulfill.
- It represents the formal contract of service that user gets.
- Letter P is used to represents provided port.
%22%20transform%3D%22translate(.5%20.5)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23c8c8c8%22%20cx%3D%2243%22%20cy%3D%2232%22%20rx%3D%2228%22%20ry%3D%2217%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(85.44094%20-101.28211%2055.90072%2047.1575%20141%2068)%22%2F%3E%3Cpath%20fill%3D%22%23dedede%22%20d%3D%22M23%2015l8%2038%2055-28z%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22188%22%20cy%3D%2229%22%20rx%3D%22109%22%20ry%3D%22109%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Fig. Provided interface
Required interface:
- It describes the operation which is provided by other components for operating properly in a specific environment.
- Letter R used to represent required port while the letter “I” is used to represent interface.
- Required and provided interface is linked to internal service by require and provided ports.
%22%20transform%3D%22translate(.5%20.5)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20cx%3D%224%22%20cy%3D%2247%22%20rx%3D%2218%22%20ry%3D%2210%22%2F%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-.31606%20-2.1596%208.8142%20-1.28997%20232%2011.1)%22%2F%3E%3Cpath%20d%3D%22M88.7%20100L73%2084.6l8.1%2016.7%201.6-16.6zM98%2025h6v9h-6z%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Fig. Required interface
Q4) b) Explain the important characteristics of real-time software architecture. (4 marks)
Characteristic of real-time software architecture are:
- They are concurrent systems and have time constraints for operations.
- Real-time systems are a complex system.
- They produce multiple independent results for multiple independent inputs.
- A real-time system contains special purpose device drivers which can be connected to sensors and actuators.
- A real-time system contains real-time input and output system with real-time operating system and real-time applications.
- The time of data arrival is not known and load can be varying at different times, thus the system is unpredictable.
- Soft and hard real-time system requires different design strategies.
Q5) a) Explain characteristic, consequences, and application of iterator and observer pattern.(6 marks)
Iterator pattern:
Characteristic:
- The client can iterate through objects without showing the internal architecture of aggregate object.
- We can iterate objects in many ways depending on application requirements.
- It is also called as cursor pattern.
- We can access the elements of an aggregate object sequentially.
Consequences:
- It provides an easy interface to the aggregate object.
- We can traverse the elements of the aggregate object. According to requirements of application and type of data structure, the traversal mechanism is decided.
- Some condition allows more than one traversal on an aggregate object.
Applications:
- We can use iterator pattern in library management system.
- Iterator design pattern is also used in Java and .Net programming.
Observer pattern:
Characteristic:
- In this, when the state of one object changes, all dependent objects are automatically updated.
- Notify operation of observers to get called when an object has to be notified of the state change occur.
- In this, one object is considered as a subject which maintains the record of observers.
- Concrete subject stores the states which need to be observed by observers.
- Concrete Observer maintains a reference to concrete subject object.
Consequences:
- Notifications are broadcasted to all objects who subscribed for state change event.
- If subject state change depends on other object states then, in that case, subject play the role of observer and other object becomes subject. In this manner, the updates and notifications can be cascaded to different levels of observers and subject.
- A subject does not have the knowledge of the concrete class of observer which can cause loose coupling between observer and subject.
Applications:
- In Computer network monitoring system, monitoring system act as observer pattern.
Q5) b) Describe singleton pattern and its significance with an example. (4 marks)
- In singleton pattern, only one instance of the class must be created and which can be used as a global point of access. In this, the class is responsible for instantiating itself.
- In this, a class ensures that only one instance of the class exists by keep tracking itself. Thus, a special operation allows a user to access the unique instance.
- There is no any collaboration of classes for accessing the singleton instance. User access the instance from the well-defined access point.
- If any other instance is present and class gets the request to instantiate itself again then it rejects the request.
- It makes the system free from global variables.
- Singleton class is supposed to encapsulate its sole instance.
- For example, there should be only one instance of antivirus scan is running in a system.
OR
Q6) Write short notes (Any two): (10 marks)
- Factory pattern.
- Proxy pattern.
- Web services.
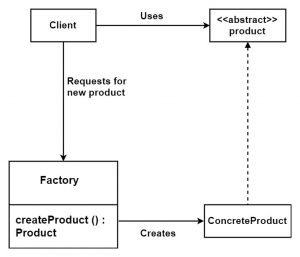
Factory pattern:
- It used to create an object without displaying creation logic to the user.
- It is used by C#, C++, Java languages. It is mostly a commonly used design pattern.
- It is easy to implement.
- When the client requires a product then it does not create it by using new operator instead of its request for dedicated factory object for the product and declare which type of object he needs to the factory.
- Now factory creates the new product and gives it to the client. The client can use this new product as an abstract product since it is cast from abstract product class.
- Client is not aware of internal implementation.
%22%20transform%3D%22translate(.8%20.8)%20scale(1.66406)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23cbcbcb%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-54.90858%2029.95363%20-21.25853%20-38.96944%2033.6%20190.6)%22%2F%3E%3Cellipse%20fill%3D%22%23cdcdcd%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-7.98158%2033.50317%20-53.89984%20-12.84075%20204.3%20.4)%22%2F%3E%3Cpath%20fill%3D%22%23d1d1d1%22%20d%3D%22M68%2090L87-16l-56%202z%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22163%22%20cy%3D%22120%22%20rx%3D%2292%22%20ry%3D%2292%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Fig. Implementation of factory pattern
- As shown in the figure, a factory class offers to create product () method which returns abstract product reference.
Proxy pattern:
- It is used to provide a placeholder for other objects to control access to it.
- It can provide an interface to file, network connection etc.
- In some cases, care should be taken that costly objects should not be fully initialized. They contain objects of high preference which acquire more resources.
- Those few methods can initialize by a proxy lightweight object.
- For example, when we open gallery application on our phone, images should be listed according to a folder and all the images do not need to be loaded at first.
- When the user enters into the folder then images are rendered by the application. After fully loaded, more operations can be performed on images.
- Thus, when we open our gallery, proxy object responds with limited information about images. High-resolution images can be loaded and rendered at next stages.
Web services:
- It provides a standard approach for application to application communication over the internet.
- Web service makes a software hosted on any site over the internet which is available as service.
- It provides application programming interface as a standard approach for communication.
- Example: For credit card validation system, the user only needs to enter the id and password for credit card and web service reports the validity of it.
- For currency converter, enter the source and destination currency with the amount then converted data will be displayed.